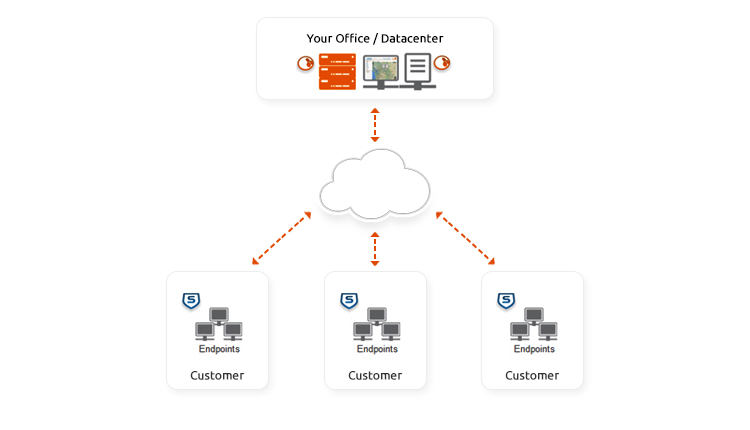
What we do for your Business
Ejaf Solution has a clear advantage when it comes to providing advanced network security solutions for enterprises – through in-depth expertise and practical experience we are focusing to be the one of security solutions system integrator in the region. Ejaf works with industry leading technology vendors and with a pool of highly skilled consultants and engineers that have designed, deployed, implemented and operated some of the most critical networks and infrastructure in the region.
15+
30
100%
4countries
Targeted threat (also known as Advanced Persistent Threat, or APT) is a very sophisticated attack and follows a fairly well-defined framework for success. An APT is more of a methodology used by attackers, rather than a piece of malware. APT Defense Framework is an integrated security framework based on intelligence sharing with real-time visibility of known & unknown threats. The APT fabric comprises of a gateways, endpoints and sandboxing components all working together to address the threats across the entire IT spectrum.The APT framework will fortify the organization and ensure mitigation of targeted and zero-day attacks.
Web applications allow employees secure access to critical business resources of the front end (website), intermediate layer (web server) and backend (database server). Web Application Firewalls (WAF) provide focused, layered web application threat protection for enterprises, custom application service providers, and SaaS providers. Using advanced techniques WAF provides advanced bi-directional defense against buffer overflows, malicious sources, cross-site scripting threats, DoS attacks and refined threats like SQL injection, cookie poisoning, and several other web application attack types.
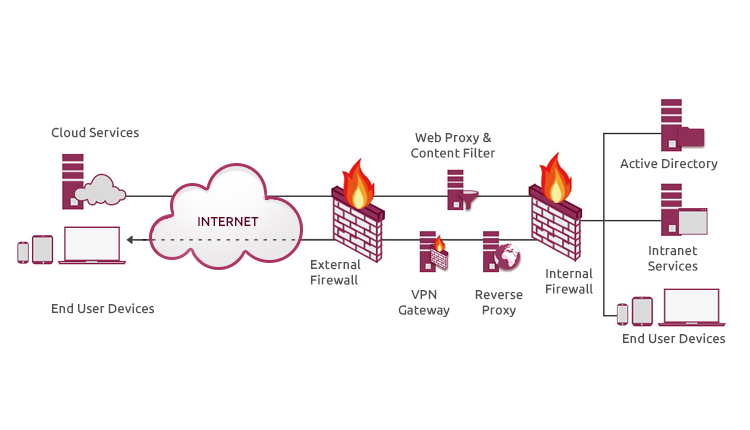
Organizations using business applications from technology leaders like Microsoft, IBM, Oracle, SAP or other popular vendors, need to deliver swift response times, uninterrupted availability, seamless access from multiple locations and have enhanced enterprise network security. The solution is Application Delivery Controller which besides load balancing, provides a set of features that maintain the security, availability and swiftness of Internet-based applications. The advanced application delivery controllers offer critical data center functions such as layer 4-7 load balancing, application acceleration, proactive application health-checks, SSL offloading, DDoS protection and DNS application firewalls.
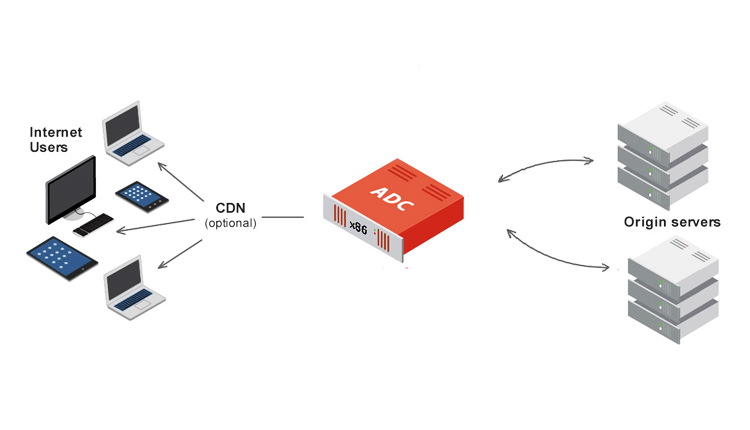
The category of firewalls are designed to filter network and Internet traffic based upon the traffic type using specific port or application being used. Next Generation Firewalls by leveraging granular application-specific security policies help detect application-specific attacks. Next-generation firewall (NGFW) can be a hardware-based or software-based network security system, based on policy that is defined and in the combinations of protocol and ports block attacks at Layer 7. Some of the features offered by NGFW are Stateful Inspection, Application Awareness, Intrusion Protection System (IPS), Multiple Functioning Modes, User Identity Awareness, and the ability to leverage external real-time updates from intelligence sources.

A vulnerability assessment is an internal audit of organization’s network and system security; the results of which indicate the confidentiality, availability and integrity of the network components. Vulnerability Assessment can also be termed as the process followed to identify inadequately secured computers and/or networks. Assessments also generally include multiple approaches for prioritizing and applying additional security actions for fixing and shielding systems from threats. Regular vulnerability assessments create a preemptive focus on overall information security and helps identify potential exploits before hackers find them. The vulnerability assessments help simplify PCI-DSS, SOX and HIPAA compliance and reduces associated costs.

Missing security updates is one of the leading threat vectors exploited by malwares. Automated patch management solution scans connected endpoints and servers to find missing patches on OS and third party applications. Automated Patch Management will help reduce delivery time for critical and high risk patches. Further, it gives you visibility on the status of current compliance levels against leading industry benchmarks. It gives you extensive reports on the most vulnerable systems and overall view of the environment.
Malware is concise of the term malicious software that is specifically designed to gain access, steal data and damage a computer without the owner’s knowledge. There are various types of malware including viruses, worms, gray-ware, spy-ware or any type of malicious code that affects a computer. Malware Protection solution ensures continual security for all activity performed by the users using any application, from any device, and at any place including proactive protection against viruses, Trojans, worms, spy-ware, ransom-ware, and new variants which emerge regularly. Connected threat defense delivers rapid response enabling faster time-to-protection and reducing the spread of malware.

In today’s world where threats evolve on an ongoing basis, organizations require to adopt a comprehensive endpoint security technology equipped with real-time protection against the advanced, latest and the unknown threats. Endpoint protection solution encompasses modern threat protection technologies for device control, anti-malware, packer variants, command and control traffic, browser-based exploits, behavioral monitoring, web threats and more. Endpoint protection provides security for file servers, PCs, desktops, mobile devices, laptops, and VDI infrastructure whilst protecting against data loss and theft.